


 |
Adversarial Machine Learning by Doug Tygar, Professor Department of Computer Science University of California - Berkeley, USA [more...] “Imagineering” an Internet of Anything by Jeffrey Voas, Computer Scientist National Institute of Standards and Technology, USA [more...] [slides] [paper] Constraint-Based Reasoning in Static Analysis and Testing by Jian Zhang, Professor & Assistant Director Institute of Software Chinese Academy of Sciences, China [more...] [slides] Software Fault Tolerance by Kishor Trivedi, Chair Professor Department of Electrical and Computer Engineering Duke University, USA [more...] [slides] |
 |
SERE 2014 brings together a broad spectrum of both researchers and practitioners who present on-going ideas, experiences, and most recent research. They can exchange their best practices for developing reliable, secure, and trustworthy software systems more effectively and efficiently. This gives the academic community an increased awareness of areas vital to the industry, while also presenting practitioners an opportunity to express their needs.
The conference has three major tracks: research papers, fast abstracts and the student doctoral program. Included are invited keynote addresses, talks, panels, and tutorials on emerging topics related to the scope of the conference. Additional workshops, more intensely focused, will also be held concurrently.
Software Quality Assurance
Special welcome is extended to contributions on the following topics, although others will be accepted as well:
 Security, Reliability, Availability,
and Safety of Software Systems
Security, Reliability, Availability,
and Safety of Software Systems
 Information and Software Assurance
Information and Software Assurance
 Fault Tolerance
for Software Reliability Improvement
Fault Tolerance
for Software Reliability Improvement
 Modeling, Prediction,
Simulation, and Evaluation
Modeling, Prediction,
Simulation, and Evaluation
 Validation, Verification,
and Testing
Validation, Verification,
and Testing
 Metrics, Measurements,
and Analysis
Metrics, Measurements,
and Analysis
 Secure and Reliable Storage
Secure and Reliable Storage
 Software Penetration and Protection
Software Penetration and Protection
 Software Vulnerabilities
Software Vulnerabilities
 Malware Detection and Analysis
Malware Detection and Analysis
 Intrusion Detection and Prevention
Intrusion Detection and Prevention
 Operating System Security and Reliability
Operating System Security and Reliability
 Mobile and Cloud Computing
Mobile and Cloud Computing
 Theory and Practice
Theory and Practice
 Benchmark and Empirical Studies
Benchmark and Empirical Studies

Organizing Committee
| General Chair | Bret Michael | Navy Postgraduate School | USA |
| Program Chair | Wen-Guey Tzeng | National Chiao Tung University | Taiwan |
| Workshop Chair | Rui Maranhao | University of Porto | Portugal |
| Student Doctoral Program Chair | Raul Santelices | Notre Dame University | USA |
| Publicity Chair | Sudipto Ghosh | Colorado State University | USA |
| Publication Chair | Yu-Lun Huang | National Chiao Tung University | Taiwan |
| Finance Chair | Eric Wong | University of Texas at Dallas | USA |
| Registration Chair | Junhua Ding | East Carolina University | USA | Webmaster | Shou-Yu Lee | University of Texas at Dallas | USA |
Steering Committee
| W. Eric Wong (co-Chair) | University of Texas at Dallas | USA |
| Sam Keene (co-Chair) | IEEE Reliability Society | USA |
| Jeffrey Voas | NIST | USA |
| Fevzi Belli | University of Paderborn | Germany |
| Karama Kanoun | LAAS-CNRS | France |
| Raymond Paul | Department of Defense | USA |
| Shiuhpyng Winston Shieh | National Chiao Tung University | Taiwan |
| Ji Wang | National University of Defense Technology | China |
Program Committee
| Doo-Hwan Bae | Korea Advanced Institute of Science and Technology | Korea |
| Ebrahim Bagheri | Ryerson University | Canada |
| Jongmoon Baik | Korea Advanced Institute of Science and Technology | Korea |
| Elisa Bertino | Purdue University | USA |
| Brahim Hamid | University of Toulouse | France |
| W.K. Chan | City University of Hong Kong | Hong Kong |
| Morris Chang | Iowa State University | USA |
| Hao Chen | University of California, Davis | USA |
| Ke-Fei Chen | Shanghai Jiaotong University | China |
| Vidroha Debroy | Hudson Alley Software | USA |
| Ewen Denney | SGT/NASA Ames | USA |
| Wei Dong | National University of Defense Technology | China |
| Xinshu Dong | National University of Singapore | Singapore |
| Mahmoud Elish | King Fahd University of Petroleum and Minerals | Saudi Arabia |
| Fu-Hau Hsu | National Central University | Taiwan |
| Chin-Tser Huang | University of South Carolina | USA |
| Yu Lun Huang | National Central University | Taiwan |
| Shih-Kun Huang | National Chiao Tung University | Taiwan |
| Chin-Yu Huang | National Tsing Hua University | Taiwan |
| Ling Huang | UC Berkeley | USA |
| Lucas Chi Kwong Hui | University of Hong Kong | Hong Kong |
| Martin Gilje Jaatun | SINTEF ICT | Norway |
| Herbert Kuchen | University of Muenster | Germany |
| Luiz Laranjeira | Universidade de Brasilia | Brasilia |
| Xuandong Li | Nanjing University | China |
| Ninghui Li | Purdue University | USA |
| Zhiwei Li | UC Berkeley | USA |
| Shundong Li | Shaanxi Normal University | China |
| Horst Lichter | RWTH Aachen University | Germany |
| Lin Liu | Tsinghua University | China |
| Peng Liu | Pennsylvania State University | USA |
| Jose Maldonado | University of Sao Paulo | Brazil |
| Rivalino Matias Jr. | Federal University of Uberlandia | Brazil |
| Eliane Martins | Unicamp | Brazil |
| Bruce Mcmillin | Missouri University of Science and Technology | USA |
| Yi Mu | University of Wollongong | Australia |
| Cu D. Nguyen | University of Luxembourg | Luxembourg |
| Thomas Noll | RWTH Aachen University | Germany |
| Phu Phung | University of Gothenburg | Sweden |
| Pierangela Samarati | University degli Studi di Milano | Italy |
| Raul Santelices | Notre Dame University | USA |
| Sahra Sedigh | Missouri University of Science and Technology | USA |
| Chii-Ren Tsai | Citigroup Inc. | USA |
| Tugkan Tuglular | Izmir Institute of Technology | Turkey |
| Komminist Weldemariam | IBM Africa | Kenya |
| Duncan S. Wong | City University of Hong Kong | Hong Kong |
| Yu-Sung Wu | National Chiao Tung University | Taiwan |
| Dianxiang Xu | Dakota State University | USA |
| Chang Xu | Nanjing University | China |
| Chung-Huang Yang | National Kaohsiung Normal University | Taiwan |
| Yuen Tak Yu | City University of Hong Kong | Hong Kong |
| Yuliang Zheng | University of North Carolina | USA |
| Mohammad Zulkernine | Queen's University | Canada |

Information for authors of regular papers
Submit original papers (not published or submitted elsewhere) with a maximum of ten pages. Include the title of the paper, the name and affiliation of each author, a 150-word abstract, and up to 6 keywords. The format of your submission must follow the IEEE conference proceedings format.
 Click
here
to submit your paper.
Click
here
to submit your paper.
Information for authors of fast abstracts
The objective of fast abstracts is to report on-going work, describe practical experiences, introduce new ideas to promote further validation, or state positions on controversial issues. Each fast abstract can have a maximum of two pages using the IEEE conference proceedings format.
 Click
here
to submit your fast abstract.
Click
here
to submit your fast abstract.
Information for authors of student doctoral program
The objective of the Student Doctoral Program is to encourage students to attend SERE and present their work, exchange ideas with researchers and practitioners, and get early feedback on their research efforts. Submit original papers (not published or submitted elsewhere) with a maximum of six pages using the IEEE conference proceedings format. Each submission should include the title of the paper, the name and affiliation of each author, a 150-word abstract, and up to 6 keywords. The first author must be a student (the advisor or non-student collaborators may be co-authors). Once accepted the paper should be presented by a student.
 Click
here to submit your paper.
Click
here to submit your paper.
Information for authors of workshops
Submit original papers (not published or submitted elsewhere) with a maximum of ten pages. Include the title of the paper, the name and affiliation of each author, a 150-word abstract, and up to 6 keywords. The format of your submission must follow the IEEE conference proceedings format.
 Click on "Workshops" on the left pane to view all the co-located workshops.
Click on "Workshops" on the left pane to view all the co-located workshops.

Conference Proceedings
The conference proceedings will be published by IEEE Computer Society Conference Publishing Services (CPS). Papers presented at the conference will also be submitted for inclusion into the IEEE Xplore and to all of the A&I (abstracting and indexing) partners (such as the EI Compendex).
Special Section of IEEE Transactions on Reliability
Authors of selected best papers from the conference will be invited to submit an extended version to a special section of IEEE Transactions on Reliability (T-Rel).

Important Dates
| November 15, 2013 | Workshop proposals due |
|
February 3, 2014 |
Regular papers due |
|
February 27, 2014 |
Fast Abstract Track due |
|
February 27, 2014 |
Student Doctoral Program due |
| March 20, 2014 | Author notification |
| April 25, 2014 (extended) | Camera-ready and author registration due |
| June 30-July 2, 2014 | Conference dates |

Public Transportation
Railway Station
- Ralston (4.00 KM/2.50 MI)
- San Carlos (4.00 KM/2.50 MI)
Airport
- San Francisco International (16.09 KM/10.00 MI) - Free shuttle available
- San Jose International (40.23 KM/25.00 MI)
- Oakland International (48.28 KM/30.00 MI)
Heliport/Airfields
- San Carlos (3.20 KM/2.00 MI)
Highway Exit
- Holly Street (3.00 KM/1.88 MI)
- Ralston Avenue (3.00 KM/1.88 MI)
Shuttle Service
- Pick-up/drop-off from San Francisco International Airport only.
- Call Hotel at (650) 598-9000 to request airport shuttle pick-up after collecting your luggage from the baggage claim.
- Hours of operations are 6:00AM to 11:00PM daily.
- Approximate 30-35 minutes for pick-up/drop-off depending on traffic.
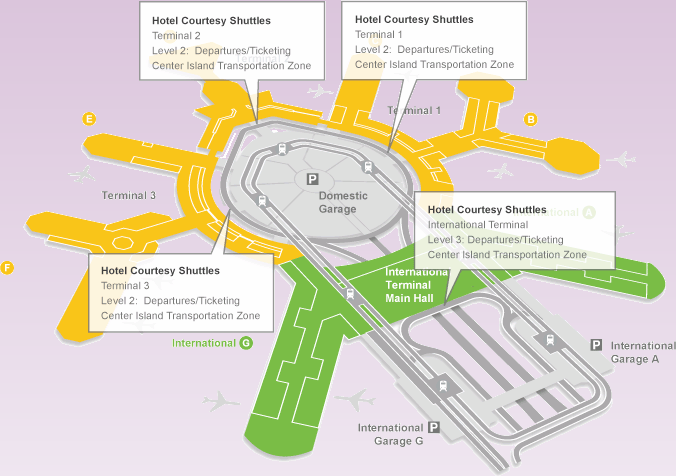
How to get to the Shuttle Area
- From the baggage claim area, go up to the departure level.
- Cross the street to the center island where you will see "Hotel Courtesy Shuttle Only".
Designated Pick-Up Points
- Terminal 1: All Domestic Airlines (Airtran, US Airways, Delta,
Frontier, Alaska)
Exit through US Airways - International Terminal: All International Airlines (Jet Blue, KLM,
China, Air Canada, British Airways, Swiss Airways, Lufthansa, etc.)
Exit through Air France - Terminal 2: Virgin American, American Airlines
- Terminal 3: Continental/United
Exit through United Gate # 8
Arriving by Vehicle
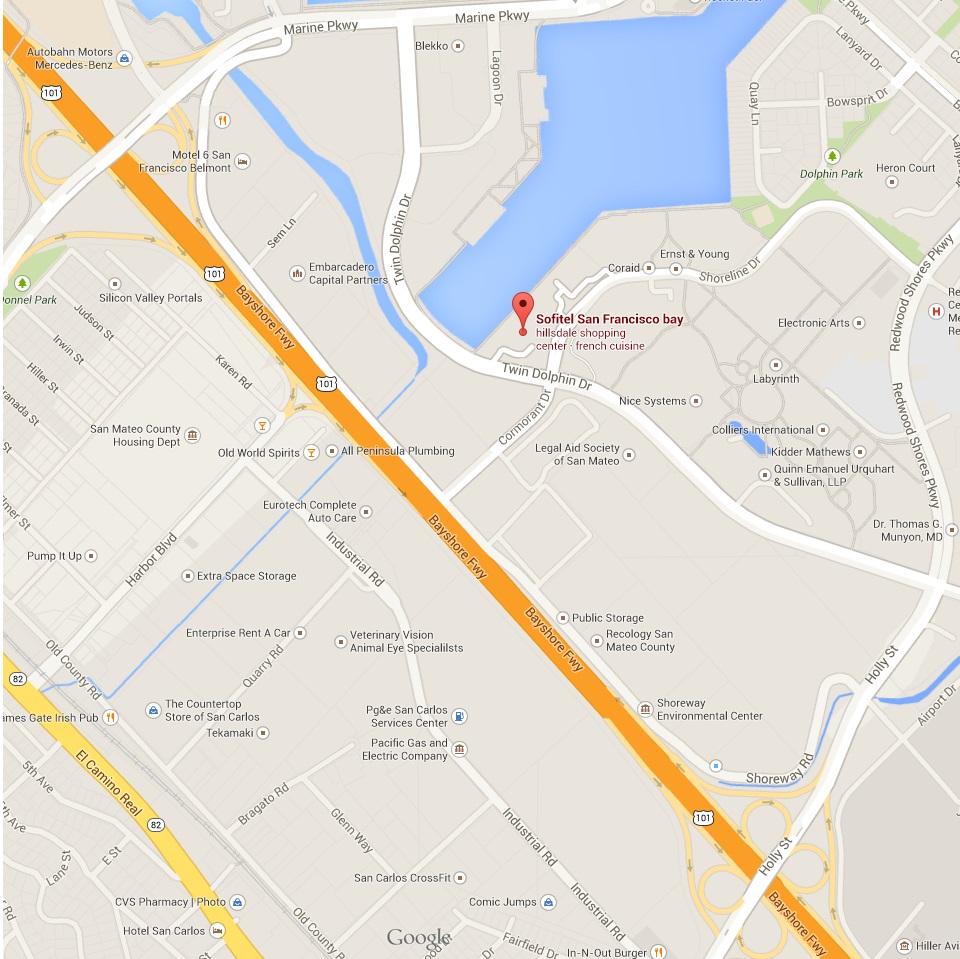
From the South
Take highway 101 north. Exit from Holly Street, then follow signs for Redwood Shores Parkway. At the second traffic light turn left onto Twin Dolphin Drive. The hotel is half a mile down on the right hand side.
From the North
Take highway 1011 south. Exit from Ralston, then follow signs for Marine Parkway. At the third traffic light, turn right onto Twin Dolphin Drive. The hotel is half a mile down on the left hand side.

Previous Conferences
 SERE 2013 -
Washington, D.C., USA
SERE 2013 -
Washington, D.C., USA
 SERE 2012 -
Washington, D.C., USA
SERE 2012 -
Washington, D.C., USA
 SSIRI 2011 -
Jeju Island, Korea
SSIRI 2011 -
Jeju Island, Korea
 SSIRI 2010 -
Singapore
SSIRI 2010 -
Singapore
 SSIRI 2009 - Shanghai, China
SSIRI 2009 - Shanghai, China
 SSIRI 2008 - Yokohama, Japan
SSIRI 2008 - Yokohama, Japan
 SIRI 2006 - Hanoi, Vietnam
SIRI 2006 - Hanoi, Vietnam

SERE 2014 co-Located Workshops
All the workshops will be held concurrently with the main conference.
 SEESED:
International Workshop on Secure Software Development
SEESED:
International Workshop on Secure Software Development
Organizer:
Natarajan Meghanathan (Jackson State University, USA)
Click here to submit your papers to SEESED 2014
 SSCPS:
International Workshop on Safety and Security in
SSCPS:
International Workshop on Safety and Security in
Cyber-Physical Systems
Organizer:
Yunwei Dong (Northwestern Polytechnical University, China)
Click here to submit your papers to SSCPS 2014
 IA:
International Workshop on Information Assurance
IA:
International Workshop on Information Assurance
Organizers:
Shih-Kun Huang (National Chiao Tung University, Taiwan)
Click here to submit your papers to IA 2014
 TC:
International Workshop on Trustworthy Computing
TC:
International Workshop on Trustworthy Computing
Organizers:
Fu-Hau Hsu (National Central University, Taiwan)
Yu-Sung Wu (National Chiao Tung University, Taiwan)
Click here to submit your papers to TC 2014
 HSCD:
International Workshop on Hardware-Software Co-Deisgn
HSCD:
International Workshop on Hardware-Software Co-Deisgn
Organizer:
Donghui Guo (Xiamen University, China)
Click here to submit your papers to HSCD 2014

For any inquiry, please contact
- Professor Wen-Guey Tzeng, Program Chair
- Professor W. Eric Wong, Chair, Steering Committee

Best Paper Award
At least one award will be presented by SERE 2014. Authors will receive a plaque signed by the President of the IEEE Reliability Society and also a cash prize (depending on the conference budget).


SSIRI 2011: Keynote Speakers
 Gerard J Holzmann Jet Propulsion Laboratory, NASA |
Verifying Complex Software Systems: the ChallengeAbstract Virtually all software applications grow in size and complexity over time.For software used in spacecraft, software size can even be shown to grow exponentially with each new mission flown, matching the growth trends seen in many other industries. This rapid growth poses a serious challenge to our ability to verify the reliability of complex safety-critical software systems. Significant progress has been made in the development of strong tool-based formal verification techniques in the last few decades, but the bar keeps rising. I will describe how we are tackling this challenge, and where the main research challenges in reliable systems design currently are. Biography Gerard Holzmann received his Ph.D. from Delft University of Technology in 1979. From 1980 until 2003 he was a researcher in the Computing Science Research Center of Bell Laboratories, in Murray Hill, New Jersey. He then moved to NASA/JPL in California to start the new Laboratory for Reliable Software, where he is currently a senior research scientist. He has published four books and many technical articles on software verification methods, image processing techniques, and telecommunication history. Dr. Holzmann is a member of the U.S. National Academy of Engineering. url: http://spinroot.com/gerard |
 C.V. Ramamoorthy Department of Electrical Engineering and Computer Sciences UC Berkeley, USA |
Software Engineering Approaches to the Challenges in Technology Education and System Development in the Software Ecosystem EnvironmentAbstract There exist several challenges in the current science, engineering, mathematics (STEM) graduate education. We are continuously inundated with great volumes of information from our portable communication devices, lap tops, television etc., continuously. We do multitasking to assimilate the information resulting developing short attention spans. Our current digital generation spends enormous amount of time on social networking, video entertainment and video games. Science and engineering subjects require long and deep attention spans to learn and to contribute. We discuss some of the successful methods that can help us to focus on the deep engineering and technology. These include video narratives, entertainment and gaming. We consider the instructional methods developed by ancient Greeks (Aristotle, Socrates etc.), and the teaching of moral principles by means of parables and narratives by Buddha and Christ. We consider the successful interest and curiosity creating violin teaching methods of Suzuki. We study the talent discovering and skill enhancing instructional methods of Montessori. The social networking and interactive type of instruction was used by Escalante to overcome academic weaknesses. The tweet- and- repeat methods of the Khan Academy also provide useful ideas for improving our teaching process using ICT technology. We propose a comprehensive cocktail (mixture) of methods as the transformative means to upgrade of STEM higher education based on similar ideas proposed and successfully used by Norman Borlaug, the Nobel Prize-winning agricultural biologist in agricultural crop production. His methods eliminated the unfortunate annual food famines in Mexico, China, and India. We propose a comprehensive software supported methods using graphical animation, using virtualization, immersion and video gaming techniques to capture interest and enhance creative skills. It is well known that we use only a small fraction of the total visual and sensual bandwidth that our nervous system and brain can process at any instant. We can expand our educational communication bandwidth input by innovative interactive graphical and aural presentations of our academic material for maximum advantage to create both interest, learning and to develop creative skills. We introduce the theme of 'Needs Engineering' into our technical educational curriculum. This topic emphasizes the importance of problem (needs) finding, problem discovery and problem anticipation. We associate a 'problem' with a specific need. Needs and necessities are mothers of invention and innovation and therefore the prime factors in creative thinking. We describe the classification of problem-solution pairs using the Remsfeld paradigm of knowns-unknowns and their importance in creative problem finding and solving. Our educational system emphasizes problem solving under a known and well understood framework of theory and knowledge. It does not lead to creative thinking beyond the 'box'. It has been said that 'main object of teaching is not just how to solve problems and give explanations, but to knock at the doors of the mind'. Problems and needs- finding approaches are indeed the mothers of creative innovation. We quote a well known ICT company CEO: "Today it is the minds, not the megahertz or the gigabytes that are scarce. Use IT (information technology) to enhance them and use them to deliver sustainable and survivable products to support our developing world". In the second part of the presentation, we shall concentrate on software ecosystems and the sustainability issues of software entities. We see a large proliferation of platforms, app's, operating systems, designs, patterns etc. The concept of software ecosystem tries to develop an environment which nurtures, supports and evolves sustainable software systems. As in the natural ecosystem sustainability implies survivability in the short term and evolution and growth in the long term under changing environments, such as operating systems, languages, platforms, services etc. We develop a simple model of growth and give some examples. The theory involves the three basic resources, namely, intellectual resource (I), manual resources (M), and physical (P) resources, essential for our living. Intellectual resources grow in accordance with the law of increasing returns (Arthur and Romer); the manual resources follow the Churchill's suggestion of using minimum manual effort, and the natural physical resources follow the law of diminishing returns. We show that the basic tenets of our growth theory are similar to theory of evolution of human development. It is not a perfect theory. We are still working on it. It is just an hypothesis and yet provides another abstract way to look at evolution and provides some valuable insights on the software engineering trends of the future. |
 Mike Hinchey Lero-the Irish Software Engineering Research Centre, Ireland |
Evolving Critical SystemsAbstract Increasingly software can be considered to be critical, due to the business or other functionality which it supports. Upgrades or changes to such software are expensive and risky, primarily because the software has not been designed and built for ease of change. Expertise, tools and methodologies which support the design and implementation of software systems that evolve without risk (of failure or loss of quality) are essential. We address a research agenda for building software that (a) is highly reliable and (b) retains this reliability as it evolves, either over time or at run-time. We propose Evolving Critical Systems as an area for research to tackle the challenge and outline a number of scenarios to highlight some of the important research questions that should be asked of the community. Given that software evolution can be seen as a compromise between cost and risk, the most pressing question to ask is which processes, techniques and tools are most cost-effective for evolving critical systems? Biography Mike Hinchey is scientific director of Lero-the Irish Software Engineering Research Centre and a professor of software engineering at the University of Limerick, Ireland. His research interests include selfmanaging software and formal methods for system development. Hinchey received a PhD in computer science from the University of Cambridge. He is a senior member of the IEEE and currently chairs the IFIP Technical Assembly. url: [email protected] |

Registration (The deadline for author registration is April 25, 2014)
 Please read all the details on this page before click
here
to start your registration.
Please read all the details on this page before click
here
to start your registration.
 Registration Fee
Registration Fee
Early Registration
(until April 25)Late Registration
(April 26 - June 28)On-Site
IEEE Member
USD 600
USD 700
USD 800
IEEE non-Member
USD 700
USD 800
USD 900
IEEE Student Member
USD 400
USD 450
USD 500
Non-IEEE Student Member
USD 450
USD 500
USD 550
 Registration Policy
Registration Policy
 Refund Policy
Refund Policy
 Paper Presentation
Paper Presentation

SERE 2014 Meeting Venue & Hotel
Sofitel San Francisco Bay Hotel
223 Twin Dolphin Dr, Redwood City, CA 94065Phone: (650) 598-9000
Mail: [email protected]
Fax: (650) 598-9383



- Click HERE for hotel reservation.
- A limited number of rooms are available from June 29 to July 2 with a group discount rate of $139.00 USD plus tax. Please make your reservation as soon as possible.
All participants staying at the hotel must use the above customized link to reserve a room. This will identify you as a SERE 2014 attendee. The hotel requires a credit card number to secure the room and to cover incidental expenses.

Final Camera-ready Submission
Please follow the instructions in the author kit you received from Bob Warner at the IEEE CPS (Conference Publishing Services) to upload your camera-ready version directly to the specific IEEE web server. Do not submit it via EasyChair, which was only for the initial submission.
 Number of Pages
Number of Pages
 Regular Paper: 10
Regular Paper: 10
 Student Paper: 6
Student Paper: 6
 Fast Abstract: 2
Fast Abstract: 2
 Workshop: 10
Workshop: 10
No extra pages are allowed.
 The submission deadline is April 30, 2012.
The submission deadline is April 30, 2012.
If you have more than one paper accepted, you need to create one profile for each
submission.
After the submission, you also need to submit the copyright release to the IEEE.

SERE 2014: Keynote Speakers
 Stephen S. Yau Information Assurance Center, and School of Computing, Informatics, and Decision Systems Engineering, Arizona State University Tempe, Arizona, USA |
Human Factors in Development of Trustworthy Service-based SystemsAbstract Over the past decade, the rapid advances and growth in deployment of service-based systems, such as the booming cloud computing systems, have had major impacts on the economy, society, and our daily lives. Today, users have grown more accustomed to accessing various online services from a wide range of computing devices, from smart phones/tablets to desktop PCs, for both business and entertainments. However, such a trend also means that more users' private and confidential information than ever is transferred processed and stored in service-based systems. This trend raises serious concerns on the trustworthiness of such systems. Substantial research has been devoted to developing new security mechanisms, network protocols, and methods to improve the trustworthiness of service-based systems. Human factors, however, have not been sufficiently addressed in the development of trustworthy service-based systems. Human factors encompass many aspects in the development of trustworthy service-based systems, from design of trust management for trustworthy service-based systems and analysis of tradeoff between system usability and security to the evaluation of users' confidence and the usability of the deployed systems. Human factors are more important in the development of trustworthy service-based systems than traditional software systems due to more complicated interactions among various participants (infrastructure providers, service providers, application developers, and users) of service-based systems. In this address, the current state of the art of human factors considered in the development of trustworthy service-based systems will be discussed, especially on how human factors are incorporated in improving system trustworthiness, such as the establishment and evaluation of trusts. Challenges and future research directions for human factors in the development of trustworthy service-based systems will be presented. Biography Stephen S, Yau is the director of Information Assurance Center and a professor of computer science and engineering at Arizona State University (ASU), Tempe, Arizona, USA. He served as the chair of the Department of Computer Science and Engineering at ASU in 1994-2001. Previously, he was on the faculties of Northwestern University, Evanston, Illinois, and University of Florida, Gainesville. He served as the president of the Computer Society of the Institute of Electrical and Electronics Engineers (IEEE) and was on the IEEE Board of Directors, and the Board of Directors of Computing Research Association. He served as the editor-in-chief of IEEE COMPUTER. He organized many national and international major conferences, including the 1989 World Computer Congress sponsored by International Federation for Information Processing (IFIP), and the Annual International Computer Software and Applications Conference (COMPSAC) sponsored by the IEEE Computer Society. His current research includes service-based systems, cloud computing, trustworthy computing, software engineering, mobile ad hoc networks and ubiquitous computing. He has received many awards and recognitions for his accomplishments, including the Tsutomu Kanai Award and Richard E. Merwin Award of the IEEE Computer Society, the IEEE Centennial Award and Third Millennium Medal, the Outstanding Contributions Award of the Chinese Computer Federation, and the Louis E. Levy Medal of the Franklin Institute. He is a Fellow of the IEEE and the American Association for the Advancement of Science. He received the M.S. and Ph.D. degrees from the University of Illinois, Urbana, and the B.S. degree from National Taiwan University, Taipei, all in electrical engineering. |
 Virgil Gligor Department of Electrical and Computer Engineering Carnegie Mellon University, USA |
Towards a Theory of Trust in Networks of Humans and ComputersAbstract We argue that a general theory of trust in networks of humans and computers must be build on both a theory of behavioral trust and a theory of computational trust. This argument is motivated by increased participation of people in social networking, crowdsourcing, human computation, and socio-economic protocols, e.g., protocols modeled by trust and gift-exchange games, norms-establishing contracts, and scams/deception. User participation in these protocols relies primarily on trust, since online verification of protocol compliance is often impractical; e.g., verification can lead to undecidable problems, co-NP complete test procedures, and user inconvenience. Trust is captured by participant preferences (i.e., risk and betrayal aversion) and beliefs in the trustworthiness of other protocol participants. Both preferences and beliefs can be enhanced whenever protocol non-compliance leads to punishment of untrustworthy participants; i.e., it seems natural that betrayal aversion can be decreased and belief in trustworthiness increased by properly defined punishment. We argue that a general theory of trust should focus on the establishment of new trust relations where none were possible before. This focus would help create new economic opportunities by increasing the pool of usable services, removing cooperation barriers among users, and at the very least, taking advantage of "network effects." Hence a new theory of trust would also help focus security research in areas that promote trust-enhancement infrastructures in human and computer networks. Finally, we argue that a general theory of trust should mirror, to the largest possible extent, human expectations and mental models of trust without relying on false metaphors and analogies with the physical world. This talk is based on joint work with Jeannette Wing. BiographyVirgil D. Gligor received his B.Sc., M.Sc., and Ph.D. degrees from the University of California at Berkeley. He taught at the University of Maryland between 1976 and 2007, and is currently a Professor of Electrical and Computer Engineering at Carnegie Mellon University and co-Director of CyLab. Over the past thirty-five years, his research interests ranged from access control mechanisms, penetration analysis, and denial-of-service protection to cryptographic protocols and applied cryptography. Gligor was an editorial board member of several IEEE and ACM journals, and the Editor in Chief of the IEEE Transactions on Dependable and Secure Computing. He received the 2006 National Information Systems Security Award jointly given by NIST and NSA in the US, and the 2011 Outstanding Innovation Award given by the ACM Special Interest Group on Security, Audit and Control. |
 Huimin Lin State Key Laboratory of Computer Science, Institute of Software, Chinese Academy of Sciences, China |
Checking Safety Properties of Concurrent ProgramsAbstract As network and multi-core systems are becoming pervasive, software systems also go concurrent. In a concurrent setting, in order to accomplish its computation task a program must cooperate with other programs by exchanging messages between them. These result in non-determinism and sophisticated interaction behaviour, making it very difficult to ensure that concurrent software systems will run safely and reliably In this talk I will present an approach to checking safety properties of concurrent programs. In this approach, concurrent programs are represented as symbolic transition graphs which can be regarded as a generalization of flow chart diagrams to allow nondeterminism and communication. Safety properties are expressed as formulas in alteration-free first-order mu-calculus. An efficient algorithm exists to check whether a symbolic transition graph satisfies the desired properties. Various abstraction techniques can be incorporated to reduce the size of reachable state space. BiographyHuimin Lin received Ph.D in Computer Science from the Institute of Software, Chinese Academy of Sciences, in 1986. He is currently a research professor and the director of the State Key Laboratory of Computer Science, Institute of Software, Chinese Academy of Sciences. He was elected Member of Chinese Academy of Sciences in 1999. Prof. Lin's research interests include concurrency, model checking, modal logics, formal methods, and tools and algorithms for concurrent systems. He is in the editorial boards of Information and Computation, Theoretical Computer Science, as well as major computer science journals in China (Science in China, Journal of Computer, Journal of Software, Journal of Computer Science and Technology etc.). He serves in the Steering Committees of the International Conference on Quality Software and the Asia-Pacific Software Engineering Conference, and has been general chairs or program committee chairs of several international conferences in the area of computer science and software. |
SERE 2014: Additional Invited Speakers
 Karama Kanoun Directeur de Recherche LAAS-CNRS Toulouse, France |
Software Dependability Assessment: A Reality or A DreamAbstract The widespread use of software systems and their ever increasing size and complexity induce many challenges to software developers and quality assurance practitioners. A fully integrated approach, based on qualitative and quantitative aspects, is needed to ensure that software dependability is correctly handled and the expected goals are reached for the final product. Dependability assessment, based on measurement, plays a vital role in software dependability improvement. Measurement encompasses both the observation of the software behavior during its development or operational life (i.e., field measurement) and controlled experimentation (i.e., experimental measurement). Field measurement requires the collection of data related to failures, maintenance, and usage environment, in order to evaluate measures such the overall software failure rate, the failure rates according to some specific (critical) failure modes, the components failure rates, and system availability. Controlled experimentation complements very well field measurement, particularly when considering Off-The-Shelf software for which, most of the time, no information is available from the development phase. The presentation will focus on dependability assessment, based on measurements. It will i) outline current approaches to measurement-based dependability assessment, with examples from real-life systems, and ii) identify some research gaps. Biography Karama Kanoun is Directeur de Recherche at LAAS-CNRS (French National Centre for Scientific Research - Laboratory for Analysis and Architecture of Systems), in charge of the Dependable Computing and Fault Tolerance Research Group (http://www.laas.fr/~kanoun/). Her research interests include modeling and evaluation of computer system dependability considering hardware as well as software, and dependability benchmarking. She has co-directed the production of a book on Dependability Benchmarking (Wiley and IEEE Computer Society, 2008). Karama Kanoun is Chairperson of the Special Interest Group on Dependability Benchmarking of the International Federation for Information Processing (IFIP), and vice-chairperson of the IFIP working group 10.4 on Dependable Computing and Fault Tolerance. She was the principal investigator of the DBench European project (Dependability Benchmarking), and managed the European Network of Excellence ReSIST, Resilience Survivability in IST. She is chairing the Steering Committee of the European Dependable Computing Conference (EDCC) and serving on the Steering Committees of three other conferences in her field of interest: DSN (the IEEE/IFIP International Conference on Dependable Systems and Networks), ISSRE (the IEEE International Symposium on Software Reliability Engineering), and SERE (the IEEE International Conference on Software Security and Reliability). She has been a consultant for several French companies (including Renault-Automation, SYSECA, Aerospatiale, SAGEM, CNES, Alcatel Espace, STNA), the European Space Agency, Ansaldo Transporti, and the International Union of Telecommunications. |
 Phillip Laplante IEEE Fellow & Professor of Software Engineering Penn State University |
Safe and Secure Software Systems and the Role Professional LicensureAbstract Licensure of certain software engineers in the United States will be required in at least 10 states by 2013 and, likely, by all US states and jurisdictions within a few years. States license engineers to ensure that those who offer services directly to the public are minimally competent. But what kinds of software systems affect the health, safety and welfare of the public? Which software engineers will need to be licensed? The answers to these two questions are both a matter of law and of science. This paper introduces some of the scientific aspects of these two questions from the perspective of reliability engineering and suggests new research directions to help answer these questions. BiographyDr. Phillip Laplante is Professor of Software Engineering at Penn State's Great Valley Graduate Professional Center. In addition to his academic career, Dr. Laplante spent several years as a software engineer and project manager working on avionics, computer aided design and software test systems. He has authored or edited 27 books and has published more than 200 scholarly papers. He is currently chairing the committee that is developing the examination, which will be used nation-wide to license Professional Engineers in the practice of Software Engineering. Laplante received his B.S., M.Eng., and Ph.D. in Systems Planning & Management, Electrical Engineering, and Computer Science, respectively, from Stevens Institute of Technology and an MBA from the University of Colorado. He is a Fellow of the IEEE and SPIE and a member of numerous other professional societies, program committees, and boards. He is a licensed professional engineer in Pennsylvania and a Certified Software Development Professional. |
 Ji Wang National Laboratory for Parallel and Distributed Processing, School of Computer, National University of Defense Technology, Changsha, China |
Formal Modeling, Verification and Refinement of Long Running TransactionsAbstract Recently, long running transactions attracted much research attention, because they are adopted in distributed systems, such as service-oriented systems, to ensure consistency. How to model and verify long running transactions is critical to improve the reliability of current distributed systems. This talk will introduce our recent work on formal modeling, verification and refinement of long running transactions in terms of a process algebra language. The start point of our work is Compensating CSP (cCSP), which extends CSP for specification and verification of long running transactions. We present an extended cCSP to support the modeling of non-determinism, deadlock and livelock, which are the three basic features of concurrent systems. A full semantic theory supporting refinement for the extended language is developed based on the theory of CSP. Leveraged by our semantic theory, the verification techniques and the tools, such as FDR and PAT, can be extended for verifying long running transactions. This talk is based on joint work with Zhenbang Chen and Zhiming Liu. BiographyJi Wang received his B.S., M.S. and Ph.D. in Computer Science from National University of Defense Technology. He is currently a professor in School of Computer of National University of Defense Technology, and the deputy director of National Laboratory for Parallel and Distributed Processing of China. He has been awarded National Natural Science Fund for Distinguished Young Scholars of China, and Professorship of Chang Jiang Scholars Program of Ministry of Education of China. His research interest includes formal analysis and verification of software systems, and distributed parallel computing. He has been an editorial board member of the Journal of Systems and Software, the Science China (Information Sciences), and a member of the Steering Committee of the International Conference on Software Security and Reliability.
|

